
Attack Surface Management Network visibility like you’ve never seen. Literally.

Unlock full network visibility, including BYOD and IoT devices, with less hassle. Identify connected endpoints and block unauthorized devices you never knew were there.
*Terms and conditions apply.
How Attack Surface Management works
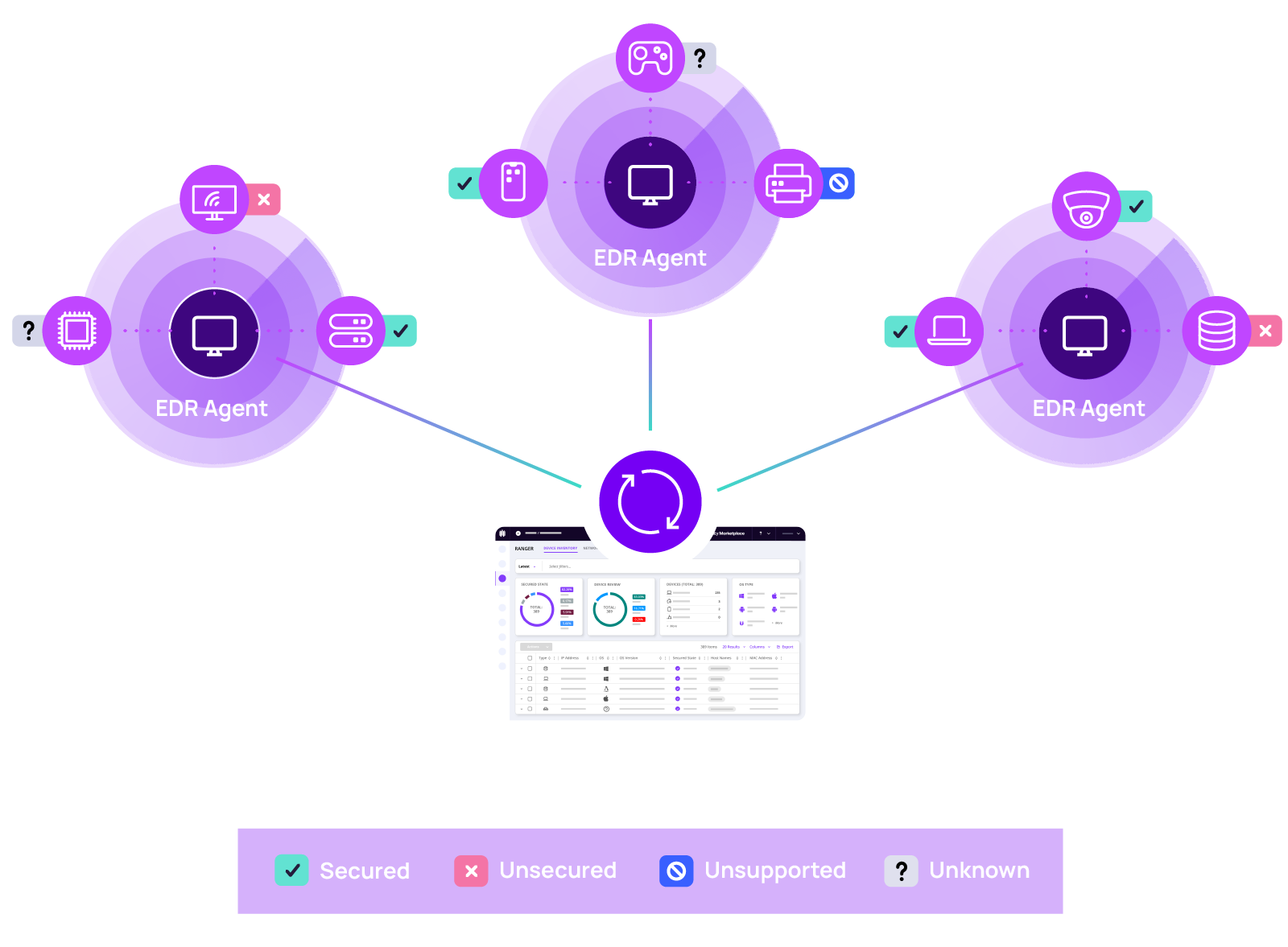
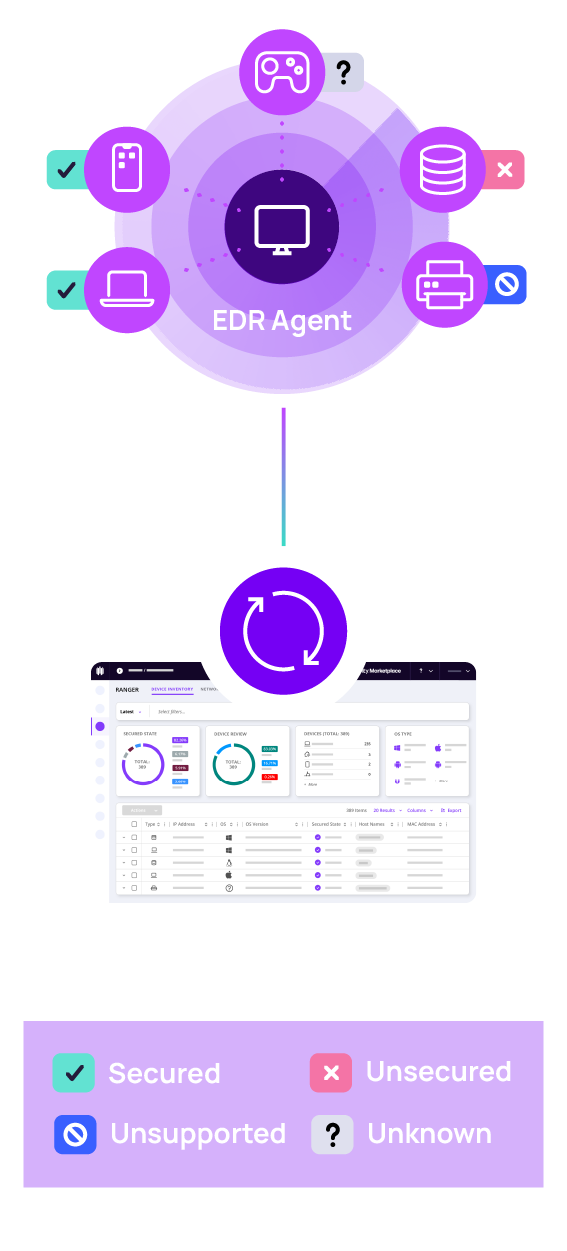
The benefits of Attack Surface Management with N‑able EDR
Get up and running in no time
Easily extend your N‑able EDR capabilities to network visibility – no need for extra software, hardware, network changes, or implementation efforts.
Forget the tedious tech work
Minimize the friction of managing various network tools through console consolidation.
Know your network – no blind spots
With Attack Surface Management, no endpoint is forgotten. Network scanning allows you to see every device, including IoT and BYOD, and monitor how they communicate.
Flexible network scanning
Control what is scanned when, and by what method, thanks to highly configurable scanning settings, available by subnet. Reduce network traffic footprint with automatic device scan management.
Unsecured but not undiscovered
Create and update asset inventories with every scan to know which endpoints are unsecured. Then, close the gaps fast with automated peer-to-peer agent deployment.
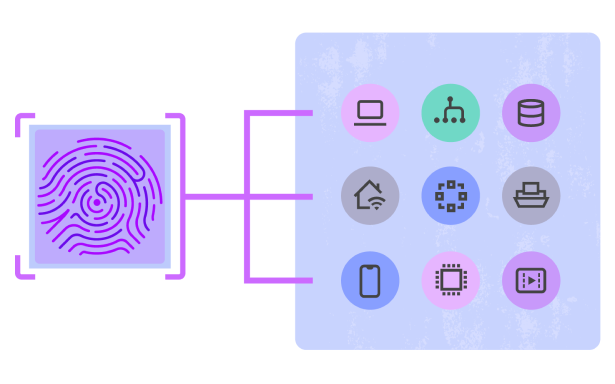
Fingerprint security at your fingertips
The advanced device fingerprinting categorizes and documents risky devices, showing due diligence for any investigations or cyber-insurance claims.
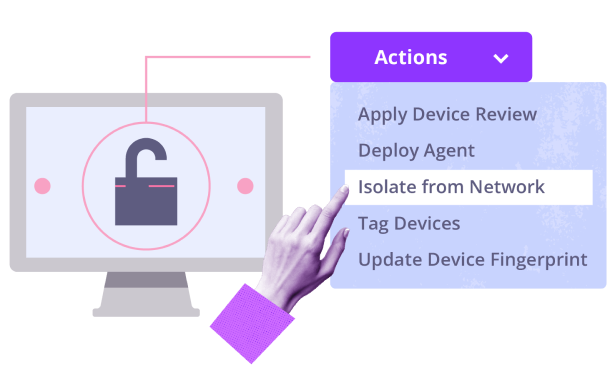
Reduce and control the attack surface
Alerts allow you to isolate any suspicious, unauthorized, or vulnerable device in just one click.
Investigate and respond fast
Hunt threats with detailed device information, find suspicious devices, and pivot to lateral movement investigations.
N‑able EDR: Attack Surface Management
Speak to an expert
You’ve seen the advantages of Attack Surface Management. Now let’s talk about how we can use them to help your business reach peak device visibility.

